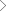CyberVigil – Complete Cyber Security Framework (Extended SOC) in a BOX
Organizations across the globe and all industry verticals are constantly facing emerging cyber threats. Increased incidents of Advanced Persistent Threats (APTs), financially motivated and targeted attacks, hacktivism and social engineering etc. are placing the entire survival of an organization at stake.
With several protection solutions in the market, organizations are struggling to select the right protection for their business and also get the best value of their investments. Most cyber security solutions do not offer complete package and today’s threats require a combination of proactive protection, comprehensive threat assessment and reporting as one solution.
Happiest Minds offers cyber security solutions that provides access to 360 degree visibility and situational awareness across security events within the organization
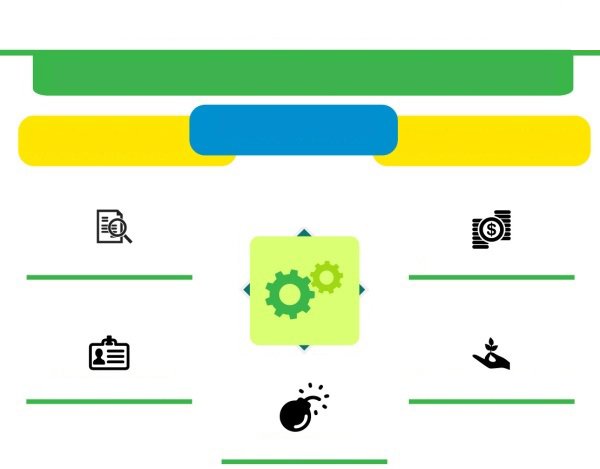
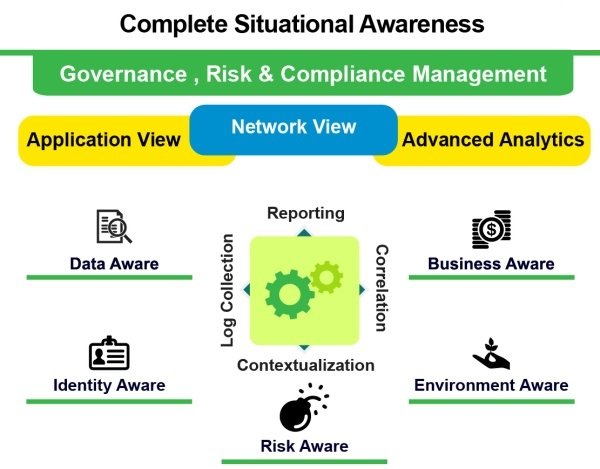
Complete Situational Awareness
Governance, Risk & COmpliance Management
Application View
Network View
Advanced Analytics
Data Aware
Identity Aware
Risk Aware
Environment Aware
Busines Aware
Reporting
Log Collection
Contextualization
Correlation
WHY CyberVigil
CyberVigil is a comprehensive cyber security solution platform that can address multiple security requirements in an easy to deploy and use model. By providing access to 360-degree visibility and situational awareness across security events across the organization, CyberVigil stands out from competing cyber security solutions and helps tackle all complex regulatory compliance reporting, policies and auditing needs with complete automation. The cyber security solution is deployed at customer premise as pre-packaged and pre-configured virtual images or dedicated appliance stack.
CyberVigil is provided “As-a-Service” with no upfront CAPEX investments and is a highly customizable and affordable solution to fit all sizes of budgets and organizations.
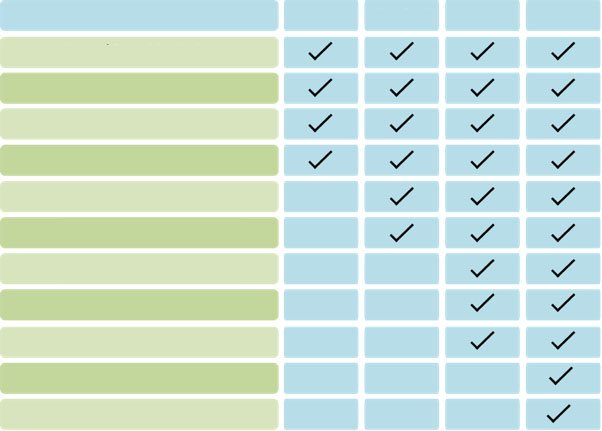
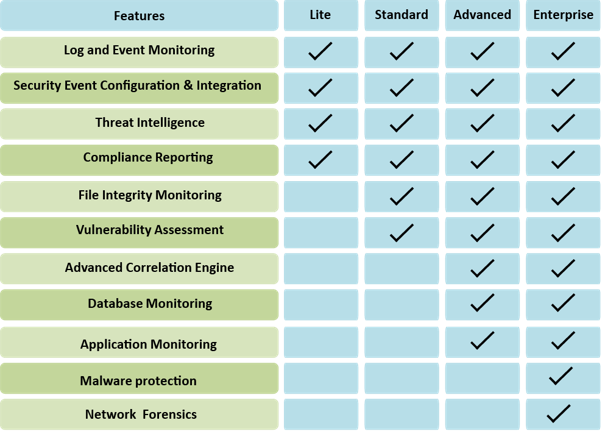
- Features
- Log and Event Monitoring
- Security Event Configuration & Integration
- Threat Intelligence
- Compliance Reporting
- File Integrity Monitoring
- Vulnerability Assessment
- Advanced Correlation Engine
- Database Monitoring
- Application Monitoring
- Malware Protection
- Network Forensics
- Lite
- Standard
- Advanced
- Enterprise
Modules
- Log Management
-
- Provide raw log retention and Searching capabilities
- Leverage Common collection layer as SIEM
- Raw Logs remain on premise and data never leaves the organization
- SIEM
-
- Provides Correlation and Alerting capabilities on the collected log data
- Monitor complete picture of security related activities
- Provide in-depth contextualization, analytics and reporting on collected data
- Threat Intelligence
-
- Integration of world leading Threat intelligence information in SIEM
- Provide rapid detection capabilities for any communication (inbound and outbound) to Known and suspicious Bad Actors across the globe.
- Compliance Reporting
-
- Included Compliance reporting packages for multiple regulatory compliance
- Detailed reporting to address and satisfy internal and external Auditors requirements.
- File Integrity Monitoring
-
- Bundled open source based FIM solution to detect any unauthorized changes on critical servers.
- Lightweight Agent with minimum CPU and Memory footprint.
- Supports Multiple Operating systems
- Vulnerability Management
-
- Bundled Service option to provide Vulnerability Assessment services
- Integration of Vulnerability information with SIEM to better threat detection
- Detailed recommendations for addressing various threats and vulnerabilities
- Database & Application Event Monitoring
-
Database Event Monitoring
- Discover all database instances including unauthorized or rogue databases
- Examine full session activity, from login to logoff for Databases
- Log database activity for a complete audit trail
Application Event Monitoring
- Provides analysis of everything from the protocols and session integrity to the contents of the application itself
- Identify data loss and compliance violations
- Detect application-layer threats