Security is fundamental to ensuring business continuity, trust, value, and reputation. And as internal and external threats or attacks have evolved and continue to infect our digital space, Zero Trust Architecture (ZTA) assumes its key role and function in preserving the system’s confidentiality and integrity of sensitive data.
The ZTA principle requires that no user, system, network, or services deployed and operating either inside or outside the network is trusted. All access must be explicitly verified leveraging authentication, authorization before granting access to any entity and continuous evaluation and monitoring is done for all such connections/ sessions.
By adopting Zero Trust, organizations gain proactive and intelligent security that is agile, monitors user actions, detects anomalies and attacks in real-time, and embraces dynamic work models in a complex environment today to offer enhanced data protection and productivity.
Happiest Minds Zero Trust Approach
The Happiest Minds Zero Trust strategy adopts an elaborate model for assessment, reduction, and management of vulnerabilities to project the impact of possible cyber-attacks, mitigate risks, and meet privacy regulations.
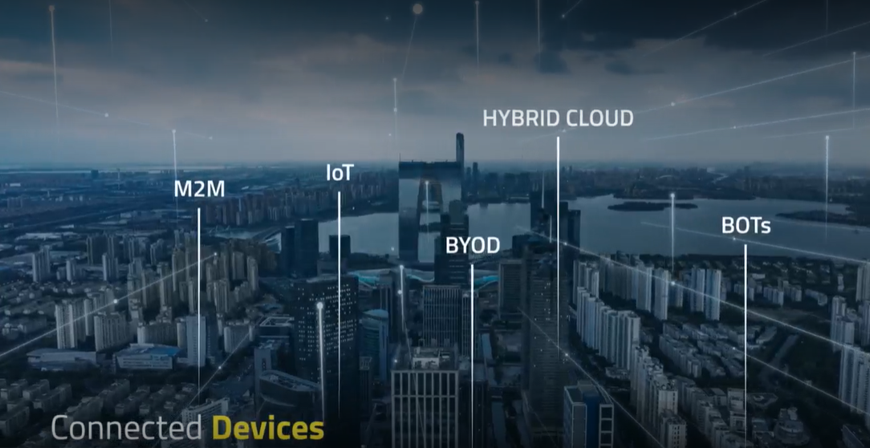
Our experts work with you to fuel your Zero Trust Security innovation and transformation strategy by: