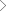OT (Operational Technology) devices are major building blocks of an effective digital transformation. With the convergence of OT with IT networks, all the OT network components like Industrial Control System (ICS), Supervisory Control & Data Acquisition (SCADA) systems, and industrial networks are being connected to IT network components such as processors, storage, and systems management. This integration of OT with IT networks in distributed systems has opened new attack vectors and vulnerabilities that were never exploited in the past. A single security breach incident can impact outages of critical services leading to severe consequences. As a result, building adequate security around a digital environment today is more complex and challenging.
Need for building an effective OT/IoT/MIoT Security Environment:
- Gaining visibility of device/machine that enters and leaves the network
- Establishing a wide array of threat detection measures
- Implementing risk-based vulnerability management system (RBVM)
- Continuous tracking of assets and its interaction between other networks
- Deploying a smart & secure remote access solution
- Building an organized configuration control over networks and devices
Creating an effective OT Security environment is not just about adopting word-class technology, it requires a strategic approach that bridges the security gap between OT & IT to deliver better visibility with simplified operations.
Happiest Minds’ proactive & transformative approach can help you address your OT/IoT security challenges by providing end-to-end assessment and integration of threat management system across your environment enabling your organization with advanced threat monitoring, detection & hunting capabilities.