In an era where businesses increasingly leverage cloud technologies for storage, processing, and collaboration, ensuring integrity, confidentiality, and availability of sensitive information is paramount. Effective cloud security measures help maintain trust, regulatory compliance, and overall business continuity in the digital landscape.
Our Approach to Fortifying Your Cloud Environment
We take a proactive and layered approach to cloud security. We combine cutting-edge technologies with strategic methodologies to fortify your digital assets and create a resilient defense against potential risks.
Our Cloud Security Service Offerings:
Plan & Scope
- Identification of stakeholders
- Identify supporting systems
- Collecting the artifacts

Perform Risk Assessment
- Probability & impact on business
- Size/complexity

Cloud Security Architecture Review
- Collect the cloud architecture
- Interview the cloud team
- Perform assessment using a well-architected framework
- Identify the security gaps

Review Documentation
- Policy manuals
- Procedures
- Narratives
- Flowcharts
- Configurations
- Assessment questionnaires

CIS / CSA Compliance Review
- Review the built-in compliance report
- Review the CIS/ CSA controls
- Identify the false positives from the built-in reports

Compliance Review
- Perform compliance checks based on the requirements.
- ISO 27001, PCI-DSS, HIPAA etc.

Review the Report with Stakeholders
- Discuss the findings with the stakeholders
- Verify the false positives
- Confirm the findings with the stakeholders

Publish the Final Assessment Report
- Prepare the final report
- Publish the report

Identify Effective Controls
- Identify Cloud Security controls
- Verify the effectiveness
- Identify the effective controls

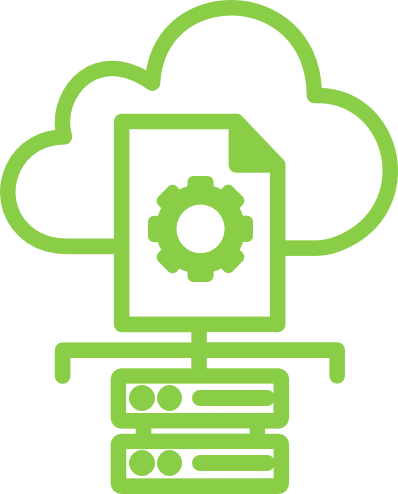
Cloud Security Posture Management (CSPM)
- Real-time visibility
- Vulnerabilities, compromised workloads, open ports, or misconfigurations
- Compliance like PCI DSS, ISO, HIPAA
- Protect against compromised credentials and identity theft

Cloud Identity and Entitlement Management (CIEM)
- Tracking and discovery of access risks
- Manage permissions
- Visibility of resource access
- Eliminating excessive permissions

Cloud Workload Protection (CWP)
- Web application protection
- API security
- Container security
- Kubernetes security

Shift Left Security
- Code scanning
- Secret detection
- Container scanning
- Function scanning
- Automated runtime protection

Why Choose Our Cloud Security Services?
- Manage privileged access across multiple clouds
- Continuous analysis of defined and used permission
- Automated detection & elimination excessive permissions
- Automated remediation of non-compliance, misconfigurations
- Compliance reports like HIPAA, PCI-DSS, ISO 27001, GLBA, SOX
- Machine learning-based anomaly detection with prebuilt detection rules