
Internet of Things (IoT) is an ecosystem of connected physical objects that are accessible through the internet. The 'thing' in IoT could be a person with a heart monitor or an automobile with built-in-sensors, i.e. objects that have been assigned…

M2M or Machine-to-Machine is a technology that enables networked devices to exchange information and operate without manual supervision or assistance. It can connect business machines and help organizations in accessing actionable data, thereby aiding them in streamlining their business, understanding…

Apache Hadoop is a 100 percent open source framework that pioneered a new way for the distributed processing of large, enterprise data sets. Instead of relying on expensive, and different systems to store and process data, Hadoop enables distributed parallel…

Big Data - the term to describe the massive growth and availability of structured and unstructured data. While the term may seem to refer to the volume of data, it also refers to the technology (tools and processes) that an…

Security testing refers to the entire spectrum of testing initiatives that are aimed at ensuring proper and flawless functioning of an application in a production environment. It aims at evaluating various elements of security covering integrity, confidentiality, authenticity, vulnerability and…
Data security refers to the combination of people, process and technology that is required to prevent unintended access, alteration and destruction of data. It refers to the various measures deployed by organizations to prevent unauthorised access to databases, internal and…
Identity and Access management refers to the processes and methodologies that are used to ensure the right access to right individuals across various information sources of an organization. This is a discipline that is fast emerging as a critical one…
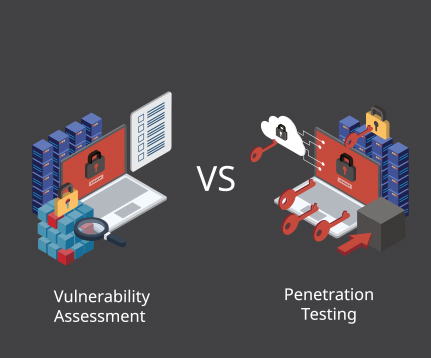
Penetration Testing is the process of identifying security vulnerabilities in computing applications by evaluating the system or network with various malicious methodologies. The end-purpose of this test is to secure critical information from outsiders who continually try to gain unauthorized…

Cyber security refers to the security concepts that are applicable across computing devices and networks, be it private, public or hybrid networks. These concepts aim at bringing about protection of network systems and data from unintended or unauthorized access, many…