The zero-trust network model implies limiting access to a company’s intellectual and sensitive data and strictly giving access to only those who absolutely need it. As traditional security infrastructure/methods are proving to be ineffective against sophisticated data breaches, the idea behind a zero-trust model (ZTM) is that anything and everything, either inside or outside of the network boundary, cannot be trusted without proper verification.
There are many security controls which are designed specifically to protect internet connections, but there are multiple entry points that can be used to launch a cyber-attack, such as VOIP systems, Wi-Fi, cloud, and WAN, among others, which are not inspected or controlled.
The Zero Trust Model
Many security/technical experts are of the opinion that the approach is difficult for preventing attackers from moving without being detected inside a network for high-value targets after they have breached the network boundary. Many recent data breaches have occurred because conventional security controls and data loss prevention tools were unable to catch the culprits who may have used fake/abstract credentials.
The growing number of remote users and the increasing use of cloud services to host various applications and services have also made it difficult for many organizations to establish and enforce a network perimeter. In a zero-trust network, no one can be trusted. We, as an enterprise, must focus on the packets traversing over the network and all incoming and outgoing traffic should be closely monitored.
Zero Trust Security Models comprise of the following pillars:
Verify the user: Passwords alone are not enough to verify the legitimate identity of a user requesting access. The best way to think about enforcing additional factors of authentication is to consider that every access attempt is secured by at least two different types of factors. For instance, it could be:
- Something you know, such as a password or a secret phrase.
- Something you have, such as a smartphone that is uniquely registered to the user and can provide push notification, which must be accepted.
- Something you are, such as your fingerprint, facial recognition, or iris scan.
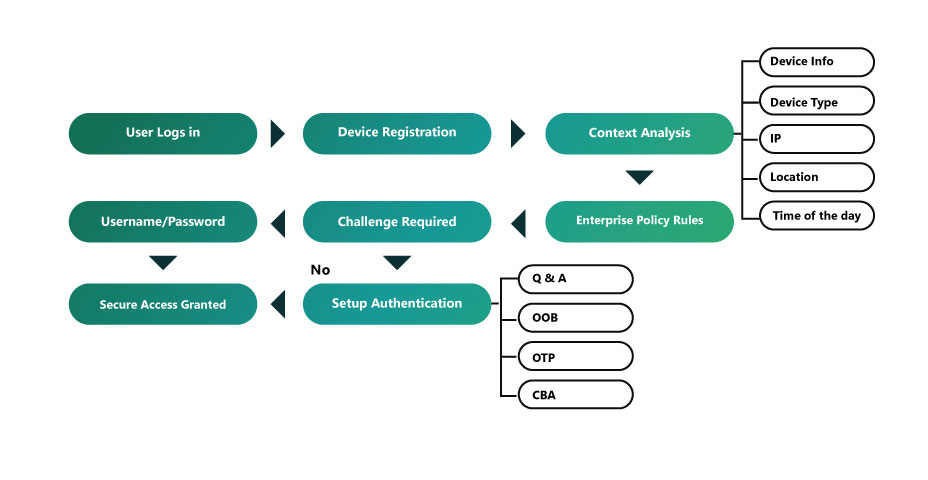
Validate the device: If a user is requesting access from a known, managed, and registered device that they use daily, you can have a certain level of confidence that the request is legitimate, especially if you have also verified the user.
Some of the additional capabilities that a device management solution provides include:
- Increase security with real-time push notifications to smart devices when users attempt to access apps that require multi-factor authentication.
- Use mobile devices as a multi-factor authentication token, supporting one-time passcode for user authentication to specific apps.
- Revoke device access to all apps with a single click to prevent data theft from lost or stolen devices.
- Ensure that only authorized applications are installed for the right users, with an inventory of apps organized by a user or a group.
Limit access and privilege: After a user has been granted access to a resource, the user’s privileges must be tightly managed. Personnel with administrative privilege are frequently targeted to exploit network vulnerabilities and gain control over business systems. With zero trust security, it is important to limit lateral movement within all resources such as applications, servers, or workstations by limiting users to only the access they need to perform their jobs.
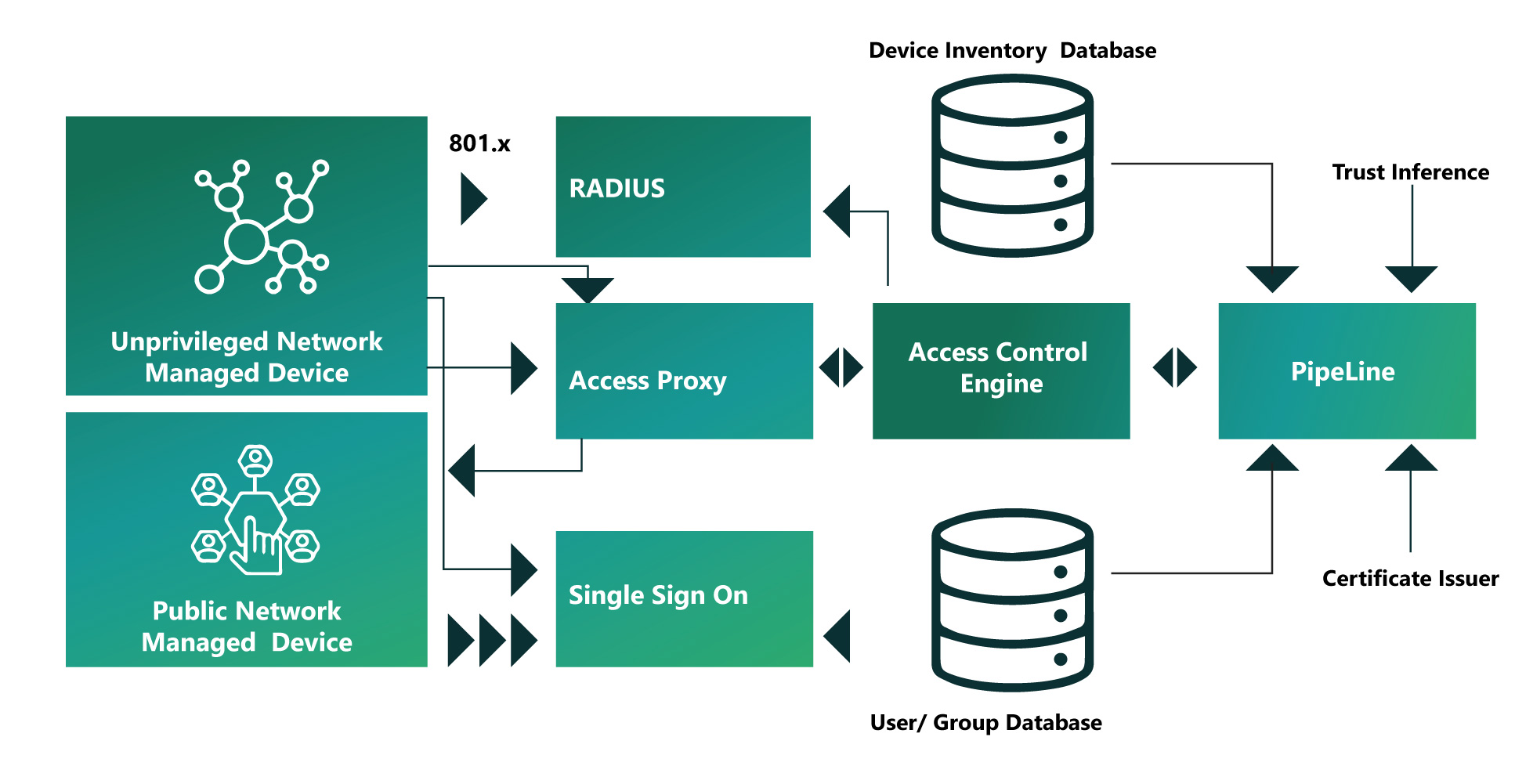
The Long Road to Zero Trust Network
Employing a zero-trust network can be challenging. Along the way, the company must redefine and streamline job roles, responsibilities and data classifications, to build an entirely new service for keeping track of devices, enable improved visibility over its applications and overall user authentication as well as access control policies.
A key aspect to keep in our mind when transitioning to a zero-trust network is that nobody can have access to internal resources until it is verified by a trusted party.
The user should be given access based on what we know about the user, and what we know about the device being accessed from our enterprise application from inside the network boundary or from outside.
We should focus mainly on securely authenticating all users, have up-to-date knowledge of roles and responsibilities and have the ability to instantly recognize abnormal user activity/ device behavior with latest technology called user and entity behavior analytics (UEBA). Our motto with the zero-level trust is to move to a model in which verification is a must.
Different Ways of Creating a Zero Trust Network
- Companies must understand and categorize an organization’s data. If we focus only on protecting network devices across the company and forget data, there will be breaches. This necessitates segmentation of the networks.
- Businesses must understand how data flows in the entire organization for every application and improve the network data flows.
- Define and improve transaction paths for correct usage of data, alert and flag it for fraud transactions when someone abuses or exploits it.
- Make automated rules across the network to inspect the policies for gateways/firewalls and alert on the right traffic to immediately inspect a possible breach.
- Monitor and inspect all traffic leaving the internal network and coming from outside the network.
- Have a dedicated network operations center (NOC) team for analyzing incoming and outgoing traffic.
Designing Security from the Inside Out
When we are planning for zero trust network, it is important to design security from the inside-out and not the other way, Businesses need to be concerned about the attack surface and focus mainly on the protecting surface network.
To protect sensitive/critical data, we should know where it is stored, how the data flows in the entire enterprise, who are the regular users, and who has access to it. Many organizations say that if you cannot trust the network to provide secure access to company assets and intellectual property, then you must have current data about the users and machines accessing them.
To enable zero trust, stringent methods for securely authenticating and identifying users/devise, is an imperative. The company’s resources should also be fully authorized, fully encrypted and authenticated based upon the state of the devices as well as user credentials.

Jyoti is a former Happiest Mind and this content was created and published during her tenure.