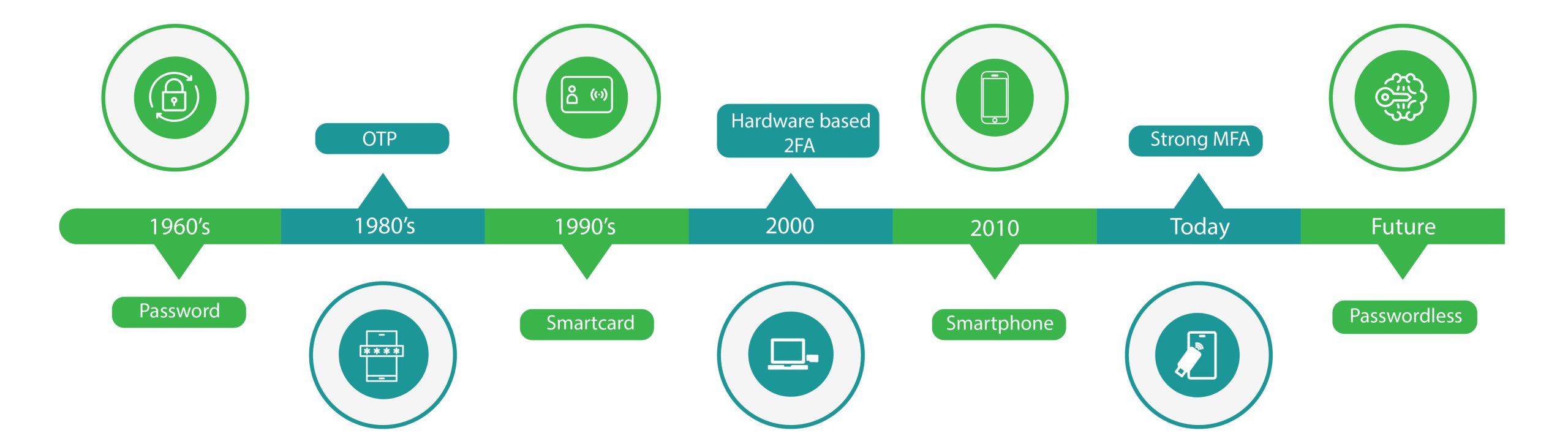
Organizations must stay relevant in the market in today’s fast-paced digital transformation era. The rising risks around passwords have grown with AI and machine learning innovations. This has made it easier for hackers to crack down on passwords that have been in use since the 1960s to a level we never witnessed before. Hence, a seamless user experience is no longer optional, as many of us still struggle to manage strong passwords and end up writing them somewhere or storing them electronically.
The shift from passwords to Passwordless authentication is a more promising solution, as 80% of data breaches occur due to stolen or weak passwords. The future of authentication must balance both seamless user experience and foolproof security.
- “The volume of password attacks has risen to an estimated 921 attacks every second globally – a 74 percent increase in just one year, a Microsoft report has said”.
- “30% security breaches caused by Weak Passwords: Good Firms 2021 Research”.
- “Verizon’s Data Breach Investigation Report says that over 70 percent of employees reuse passwords at work”.
The Passwordless Revolution: Igniting Transformation in Authentication
Embarking on the Voyage of Passwordless Authentication
The voyage of Passwordless authentication may involve challenges, discovery, and growth. It symbolizes a commitment to enhancing security, simplifying authentication processes, and embracing the future of digital access.
Passwordless is a solution that authenticates a user without relying on passwords where the latter is not even used as a substitute. Passwordless uses a combination of alternative factors like security keys, retina scans, biometrics, OTP, QR codes, push notifications, and mobile applications to verify users’ identities.

Traditionally passwords are stored in a directory/database. Similarly, in passwordless, we store alternative methods instead of Password, like retina scan for first-time users to extract the numerical data, which is verified and stored in the database. So, the next time the user tries to log in to the system, he/she can compare the data with the one already stored in the database. Biometric authentication is one of the safest options to consider, as it is difficult to manipulate the unique features of every individual.
Passwordless authentication works using a pair of public and private key. The public key is stored on a server, and the private key is stored on the user’s device. It can be unlocked only using an authentication method, e.g., push notification, retina scan, or fingerprint. After the private key is unlocked, the user’s system verifies it with a public key stored on the server.
Implementing a fully passwordless authentication is challenging as almost all end applications use passwords as the only authentication factor. Hence, we can have a password at the backend and use passwordless methods in the front end to authenticate while eliminating the former to adopt a passwordless seamless process.
Some popular Passwordless methods available in the market are:
- FIDO2 and WebAuthn: FIDO2(Fast Identity Online) and WebAuthn is a standard that promotes passwordless authentication using hardware-based security keys or biometrics.
- Biometric authentication: Using unique physical features like fingerprint, facial recognition, and voice recognition to authenticate without using a password.
- Mobile Device Authentication: Verify login attempts by approving them on a trusted mobile device, removing the need for password entry. We can utilize mobile-based authentication methods such as push notifications, SMS verification codes, or mobile apps.
- Adaptive authentication: Adaptive authentication is a method that adapts the authentication requirements in real-time by considering contextual factors like user behavior, device information, and network context.
- Hardware tokens: These are physical devices that generate one-time passwords.
- Email-Based Authentication/Magic link: Users receive a time-limited login link via email to authenticate.
The Passwordless journey can be divided into phases for its seamless implementation:
- Reduce the reliability of passwords as primary authentication in a gradual manner by replacing them wherever possible.
- Choose the safest authentication methods suitable for the organization based on use cases and design an authentication workflow.
- Eliminating passwords and selecting multiple authentication methods using a single factor is not advisable.
- Procure hardware or software according to the authentication method chosen.
- Educating users to adopt a new authentication mechanism.
Passwordless based MFA
MFA (Multi-Factor Authentication) and passwordless involve using multiple authentication methods to validate the user’s Identity. Most MFA solutions in today’s market have a password as a primary authentication factor and give multiple other methods as an option to choose from. On the other hand, Passwordless Authentication eliminates passwords from the list of methods available for the user to register.
Why Passwordless?
Some benefits of Passwordless authentication are:
- Smooth User experience – Using complex passwords creates frustration, which can be avoided by adopting Passwordless for a smooth user experience.
- Saves IT time and Cost – We can reduce the burden on the helpdesk by eliminating password-related tickets, which reduces costs.
- Strong Security – By using Passwordless, we can eradicate password-based attacks making it impossible for hackers to breach security.
Though Passwordless is more secure than passwords, no solution can guarantee 100% safety. We can only make the methods as complex and safe as possible to deter hackers from spoofing. Passwordless authentication becomes a better solution by combining Passwordless with multifactor authentication to enhance security and single sign-on to improvise end-user experience.
From Complexity to Simplicity: Embrace Passwordless Authentication with our Services
At Happiest Minds, we deliver the finest Passwordless authentication solution by harnessing the capabilities of various cutting-edge methods such as FIDO2, biometric authentication, and adaptive authentication. Our expertise lies in understanding each organization’s unique needs and requirements and tailoring a passwordless solution that aligns with the organization’s goals and security objectives. Happiest Minds’ catalog of services includes (but is not limited to) end-to-end IAM services – Advisory, Implementation, and ongoing support – around Identity Management, Access Management, and Privileged Access Management.

is working as Senior Software Engineer at Happiest Minds, bringing over five years of valuable experience in the cybersecurity IDAM domain. She has excelled in designing and implementing robust security measures, specifically focusing on access management and MFA solutions. She is dedicated to continuously improving her skills to address the evolving challenges within the cybersecurity landscape effectively.








