In the current technology trend, Internet of Things (IoT) adoption is getting simpler to satisfy the customer requirements and the industry standards. Most industries think about the IoT as an assortment of short-range wireless technologies that interface devices to the Internet for some helpful reason. Most current IoT applications appear to fall into that class. However, that mindset is changing and technology too.
Based on the observation and utilization of IoT devices for multiple use cases, the present most popular technologies have set up boundaries. One conspicuous most extreme range is 10-30 meters. Bluetooth, ZigBee, Z-Wave, 6LoWAPN, 6TiSCH and 802.15.4-based technologies utilize this figure, as a rule. However, longer ranges are possible under favorable conditions. Wi-Fi is said to have a most extreme usable range of 100 meters, however, it is regularly not as much as that, and we all have pleasant experience and range coverage challenges.
The most interesting part is that we have a wonderful IoT solution for long range communication, and the technology is none other than the Low Power Wide Area Network (LPWAN). LPWAN most characterizes long range as up to 10 km, but it relies upon the radio antenna framework utilized. The scope of a radio sign is dictated by numerous factors: frequency of operation, transmitter power, antenna gains, receiver sensitivity, antenna height, physical obstructions (e.g., buildings and trees), data rate, and noise and interference. While all are significant, the one that conveys the most weight is frequency, as always, the game changer.
Well, long range is fine, but the major question is about the power consumption and the battery life. There are various approaches to address low-power, long-range IoT, however the three main competitors now are Sigfox, LoRaWAN and NB-IoT (narrow band IoT). Each has a separate set of characteristics that engineers may like, however typically, a solution will use either. Today we are discussing much more about the LoRaWAN managed by LoRaWAN Alliance.
At the time of design, always we need to take care of IoT standards based on the implementation region. In case of LoRa, which means long range, that uses the 902- to 928-MHz unlicensed band in the U.S. and the 868-MHz band in Europe. Typical operating frequencies are 915 MHz for the U.S., 868 MHz for Europe. And 433 MHz for Asia. Also has a variable packet size ranging from 51 to 222 bytes, with at least 13 bytes of packet payload.
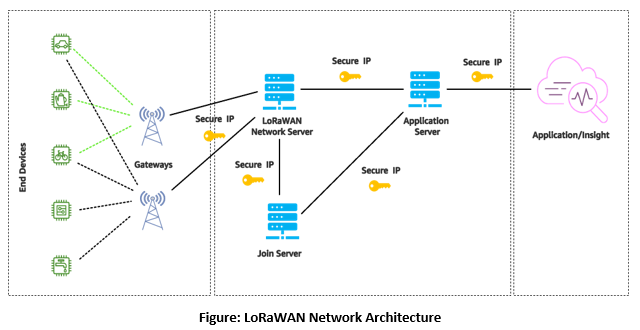
From the above end to end architecture diagram, we can find that each communication will be secured IP based communications in LoRaWAN. In the LoRaWAN network architecture, gateways are connected to the network server via standard IP connections, while end-devices use single-hop wireless communication to one or many gateways. All end-point communication is bi-directional and supports operations such as multicast, enabling software upgrades over the air or other mass distribution messages to reduce the on-air communication time.
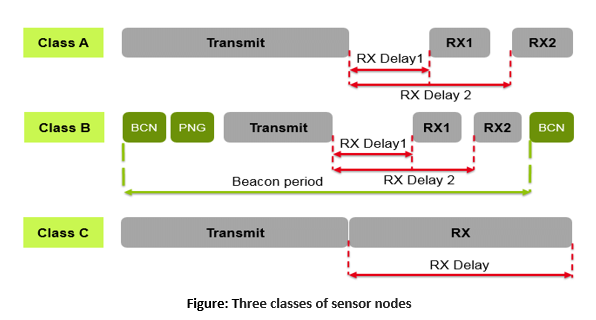
Contingent upon the sort of application, the LoRa Alliance characterizes three classes of sensors.
Class A: The sensor node periodically sends packets to the gateway module. In the wake of finishing the sending cycle, the node keeps the receiver active for a noticeably short period, in which it can get information from the gateway. After completing this cycle, the sensor enters sleep mode to save energy. Likewise, the duty cycle boundary restricts the maximum number of packets a sensor node can transmit in one day.
Class B: Not at all like class A, this kind of sensor node has programmed receiving time slots. Hence, it becomes active more often and anticipates messages from the gateway module.
Class C: This is the most minimal energy efficiency class because the sensor keeps the receiver constantly active, having the option to get messages from the gateway module at any time.
At the time of design itself, another question arises, and for sure, that will be on security. LoRaWAN is one of the few IoT networks implementing end-to-end encryption. Let us dig more on security and understand it better. LoRaWAN security design adheres to state-of-the-art principles: use of standard, well-vetted algorithms, and end-to-end security. LoRaWAN MAC and application messaging are origin authenticated, integrity protected, replay protected, and encrypted.
LoRaWAN security uses the AES cryptographic primitive combined with several operation modes: CMAC (Cipher-based Message Authentication Code) for integrity protection and CTR (counter) for encryption. Each LoRaWAN device is personalized with a unique 128-bit AES key (called AppKey) and a globally unique identifier (EUI-64-based DevEUI), both of which are used during the device authentication process.
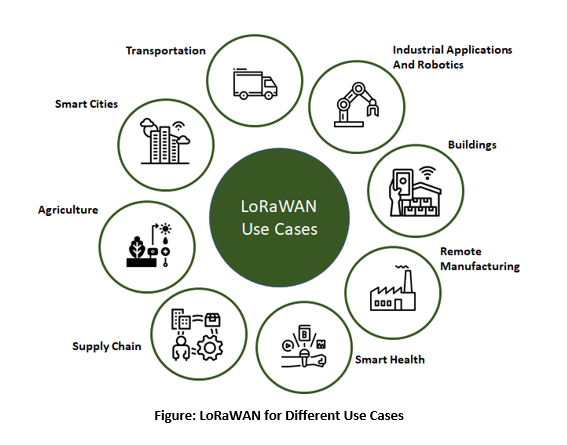
Finally, it is all about bringing a value-added solution into different use cases. The applications for LoRaWAN are extremely broad. They include utilities, trucking and logistics, smart city and parking, agriculture and farming, intelligent building, monitoring of remote things like trash, farm fields, water pipes, gas lines, and the list go on as listed in the below diagram.
We have multiple great experiences in building the LoRa solutions and some of the case studies are into precision agriculture, energy industry and in smart buildings in wider communities.

is working as a Lead Business Analyst at Happiest Minds Technologies.
He has 8 years of IoT industrial products design and development experience. He won multiple fellowship awards from Internet Society (ISOC), South Asian Networks Operator Group (SANOG), Asia Pacific School on Internet Governance (APSIG), and recognized in 2016 and 2017 as one of the Top 8 IoT Thought Leaders for his contribution towards the advancement of IoT in India. He is actively involved in the Internet Engineering Task Force (IETF) working groups to contribute to IoT protocols standardization and research-based contributions in IEEE, APAN and many more conferences and journals. One of the Internet Society (ISOC) trained moderators for the ‘Building Wireless Community Networks’ in India.