Do you have Rupee five hundred and some 10 minutes to spare? Then you can have access to billions of Aadhaar card details. Sounds scary, isn’t it?
As much scary as it sounds, this is the truth of the technology at the cost of which billions of Aadhaar details are at today. The irony to this is that the same human intervention created an intelligent and critical initiative like Aadhaar and the same human intervention weakened the entire system by creating privacy doubts and hacking vulnerabilities.
So how do we solve the human challenges posed by hackers who know every angle to the system and are always one-step ahead of the authorities? There has to be a technology that can make UIDAI system robust and trustworthy for its hundred crore subscribers and also allow the target audience with some of the effective Government programs:
- Benefits of DBTL, PDS, Scholarships & Pensions (NSAP)
- Linking Usage: Bank Accounts, LPG Connections, Ration cards, NREGA cards
- Authentication: UIDAI, eKYC
Blockchain Technology applied to Aadhaar system will help make the system robust and trustworthy. The Blockchain Aadhaar system will restore their Fundamental Right to Privacy under the Constitution of India, also accentuated by the Supreme Court’s landmark judgment. The system will have the following abilities:
- Multiple Copies – With numerous copies to compare and distributed across multiple locations, there will not be a single loophole to hack.
- Watchdog – The system should have a consensus algorithm which runs on a distributed network and decides which version of data is valid.
- Secure- The system should provide a tamper-free environment for the participants in the network through a self-reviewing system
- Smart Contracts – The system should provide a mode of exchange which will define the rules and penalties just like a regular contract. It should also automatically enforce these obligations, so there is no misuse and unwarranted access to anyone other than the designated authorities or people.
- Open Technology Standards for increased innovation, participation and efficiency.
While Blockchain Technology may sound like an easy way to restore the sanctity of the Aadhaar system, the implementation entirely depends on the government agencies given the backdrop of Virtual IDs that has a limited period and limited demographic details access. As a starter, the Authorities should empower the individual citizen to decide who gets to see his/her limited demographic information and for what time, while this information is validated by the Watchdog (the algorithm). The Blockchain Aadhaar system should also provide controlled access to the service providers so that they verify the required data as well as allow the authorities to be watchful of the data being accessed.
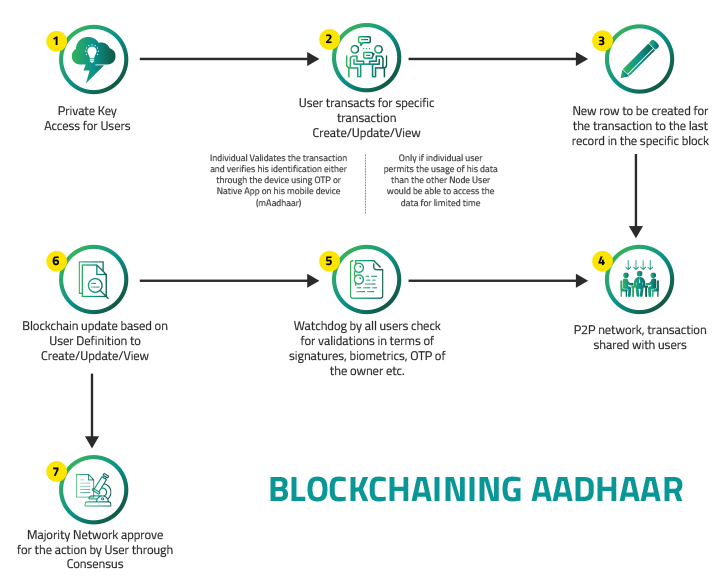
Blockchain Technology is a distributed database shared among a network of devices, all of which must approve a transaction before it can be recorded. So, it is essentially a universal ledger of digital records. One that is shared between various parties (P2P-Peer-To-Peer) and can only be updated by consensus of a majority of the participants, where once the information is entered, can never be deleted.
Adding to the safety measure, we can also introduce the existing OTP technology where the user gets the power to authenticate any information only by validating it through the OTP either received on his phone or application like mAadhaar, which would be like a node for the users to verify. The use case can follow the below process:
- The User has a private key that has been created by himself which allows him to access his information through Node or relevant app.
- Vendor like telephone agency initiates a request to verify the user’s Aadhaar Details, or Citizen wants to update specific information on his account (possible online only or visit Aadhaar Enrollment Centre)
- OTP received by the user on his registered number or email to validate which details which Agency has asked for the data validation and what data is required. OTP is validated
- System triggers this transaction to create a record in the existing block of the user data.
- The transaction details are relayed to the network, which includes all users (defined by UIDAI) including:
- UIDAI
- Users
- Government Officials (Central or/& State)
- Third-party Vendors (Telephone, banking, Insurance, etc.)
- Security Organizations
- Technology Vendor Partners
- Other Peer-To-Peer Network users
- Data Access to be provided or updated is checked for validations like OTP or signature or biometrics (if user initiates from home environment)
- Blockchain update based on user requirement
- P2P network approves, and data gets updated, and same is relayed to the User
The advantages of this process would include:
- Data Secure for users: The Users would be able to block access to his/her information based on validation through his device/node if he feels he does not want to share the information
- Data Access Authentication by User
- Reuse of current OTP feature
- Increased Trust as P2P network
However this also comes with a set of challenges like enhanced network security, more users to be added who not only perform as a Watchdog but also system partners and data hackings as digital thieves are always one step ahead of whatever anyone does to secure their properties.
Please note: This blog is part of a series of Blockchain articles. Through these articles we explore about Blockchain – The technology, the hype, the opportunity, the do’s and the don’ts.

Adarsh is a former Happiest Mind and this content was created and published during his tenure.





