Remember the good old days when we discussed about number of computers getting infected by malicious content? Ironic- considering we are discussing about malicious content and ‘good’ in the same breath. Well, if you think of the meteoric rise of ransomware in past few years – the good old Trojan looks almost friendly and harmless. As opposed to a few thousand computers getting affected then, we speak of countries and continents getting infected by malicious content now. What’s more, there is actual ‘ransom’ you have to pay to get access back to your data residing on your device in your very own organization. Welcome to the age of Cyberwar! Are you carrying enough ammo to protect yourself?
Since the day the first ransomware attack was launched, the information security world has been abuzz with various control measures to be adopted to arm yourself against a ransomware attack. What most of them do miss to point out is that, we are not just talking about the infamous crypto-ransomware, there is a plethora of ransomwares out there such as Leakware/ Doxware, Crysis, Samsam, Cerber, Locky-Zepto just to name a few. To protect yourself against a vast variety of malicious content you need a healthy mix of different controls in place such as 1) Perimeter Security (Email Security Gateway, Firewalls, Web Security Gateways), 2) Endpoint Security: Traditional Antivirus, Endpoint Security AND/OR End point privilege access management 3) Patch Management, 4) Vulnerability Scanners, 5) Application Whitelisting/Blacklisting/Gray Listing, 6) Port Security so on and so forth. Above all, robust and continuous back-up in place.
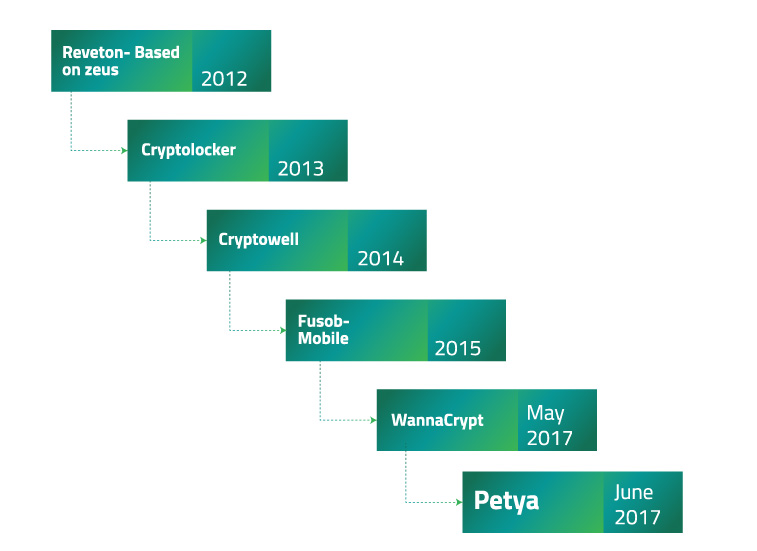
Ransomware Evolution:
While various levels of controls are identified for ransomware protection, the most vulnerable and frequently exploited is the END POINT. With new variants of malwares and ransomware being introduced in market- traditional endpoint security alone is no longer sufficient. Ransomware-as-a-service is an undeniable reality which arms the most amateur cybercriminal with enough ammo to launch their own customized attacks. The traditional end point solutions can be helpful when you know what you’re looking for – but when it comes to ransomware, there are new variants coming out every day. Signature based end point protection will no longer suffice. Hence, next gen end point protection solutions clubbed with end point privilege access management solutions are the need of the hour- which may function independently or in conjunction with the traditional end point security.
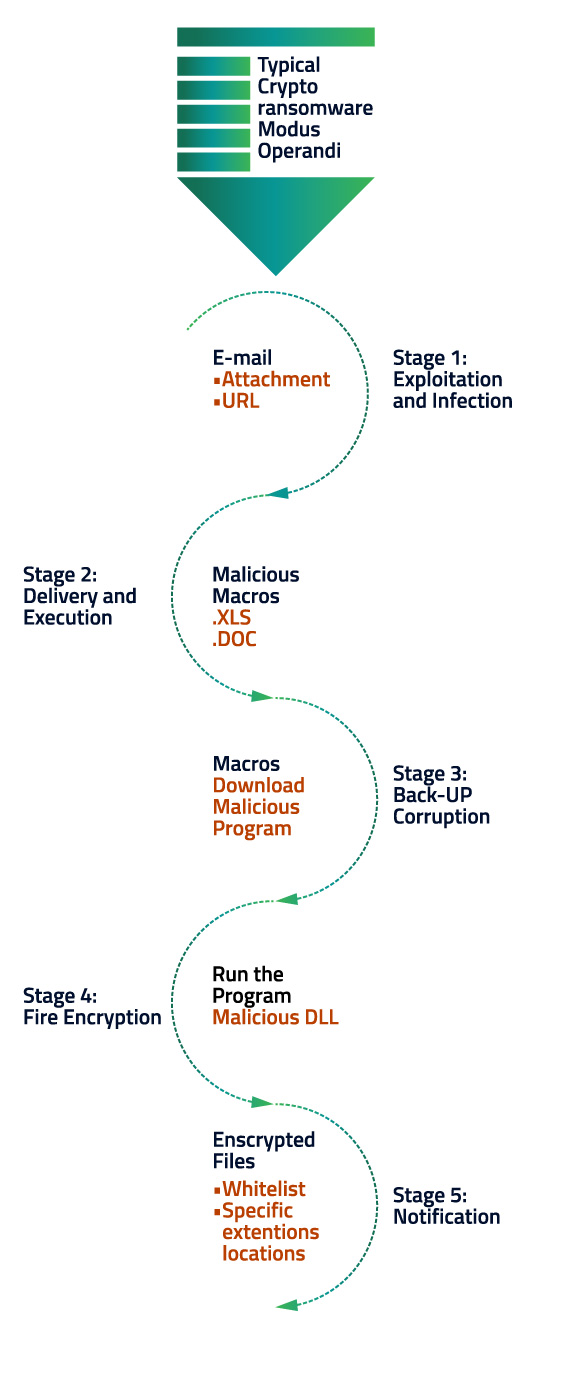
The next gen end point security solution and privilege access management solutions also offer behavioral analytics i.e. analysis based on machine learning, artificial intelligence based threat detection measures etc. These advanced features make the next gen end point security solutions much smarter than the traditional tools which depend heavily on signature or heuristic based prevention measures of malicious content.
It is also important to look for end point security tools that also offer sandbox analysis, specific in-built ransomware policies, end point isolation (after detection) with minimal effort, rollback of the changes, application white/black/grey listing capabilities, activity recording. Integration with SIEM, network security and threat intelligence solutions can significantly improve the overall adaptability of the end point security suite.
End point privilege escalation is the most frequently exploited feature by the attackers and is yet the most neglected and still highly vulnerable areas an end point security tool that offers Administrative rights removal on end points without affecting the user capabilities is the key to avoid such attacks
Unfortunately, there is no single vendor in the market today offering all the above prevent & protect capabilities in an end point security suite.
The Best Defense Strategy at End point: Comprehensive approach to fend off any ransomware at the end point must work on the Detect, Protect, Sustain approach. Detection methodologies – combination of manual as well as tool based; needs to be adopted to identify ransomware including in stealth mode. Any new suspicious content entering the network should be blocked and reported. Protection controls on the endpoint should focus on application whitelisting/blacklisting/grey listing, enforcement of ransomware protection policies, blocking unauthorized access, RBAC, removal of admin access among others. Any Defense strategy is ineffective without a proper Sustain plan in place which must include but not limited to continuous monitoring, Incident Management and Analysis, patch management, internal audits, periodic reviews, policy updates and most important regular backups and testing
Whether you decide to stay with traditional end point security or upgrade to next gen end point security and end point privilege access manager is your prerogative. However, as popular proverb goes on to say “a chain is only as strong as its weakest link”. Don’t let inefficient end point security control compromise your organization’s security on the whole – because like it or not, ransomware is here and evolving as we speak. Who knows? – you could be the next?

Susmita is currently working as Technical Manager at Happiest minds with close to 12 years in IT industry. With 8+ years in Enterprise Security, ‘Privileged Identity and Access Management’ and Identity and Access Management (IAM) Consulting are her area of expertise. Passionate in exploring the emerging trends in information security technologies. In her free time, she likes to explore various areas of creativity like sculpting, mural painting and writing.






