Introduction:
In today’s interconnected world, where data flows ceaselessly across networks, ensuring security and efficient data transfer is paramount. One of the key technologies that enable network administrators to achieve these goals is Deep Packet Inspection (DPI). DPI came into the picture in the network industry as a response to the growing complexity of internet traffic, the need for enhanced Quality of Service (QoS) and security measures, regulatory requirements, the shift towards application-centric networking, and the desire for monetization and service differentiation. Its ability to inspect and analyze packet contents at a deep level made it a crucial technology for modern network management and optimization. This blog post aims to shed light on the concept of DPI, its significance, benefits, and potential concerns.
What is Deep Packet Inspection (DPI)?
Deep Packet Inspection, often abbreviated as DPI, is a sophisticated technology used to analyze and monitor network traffic at a granular level. Unlike traditional packet inspection, where only the packet header is examined, DPI delves deep into the packet’s payload, inspecting the actual data content.
How Does DPI Work?
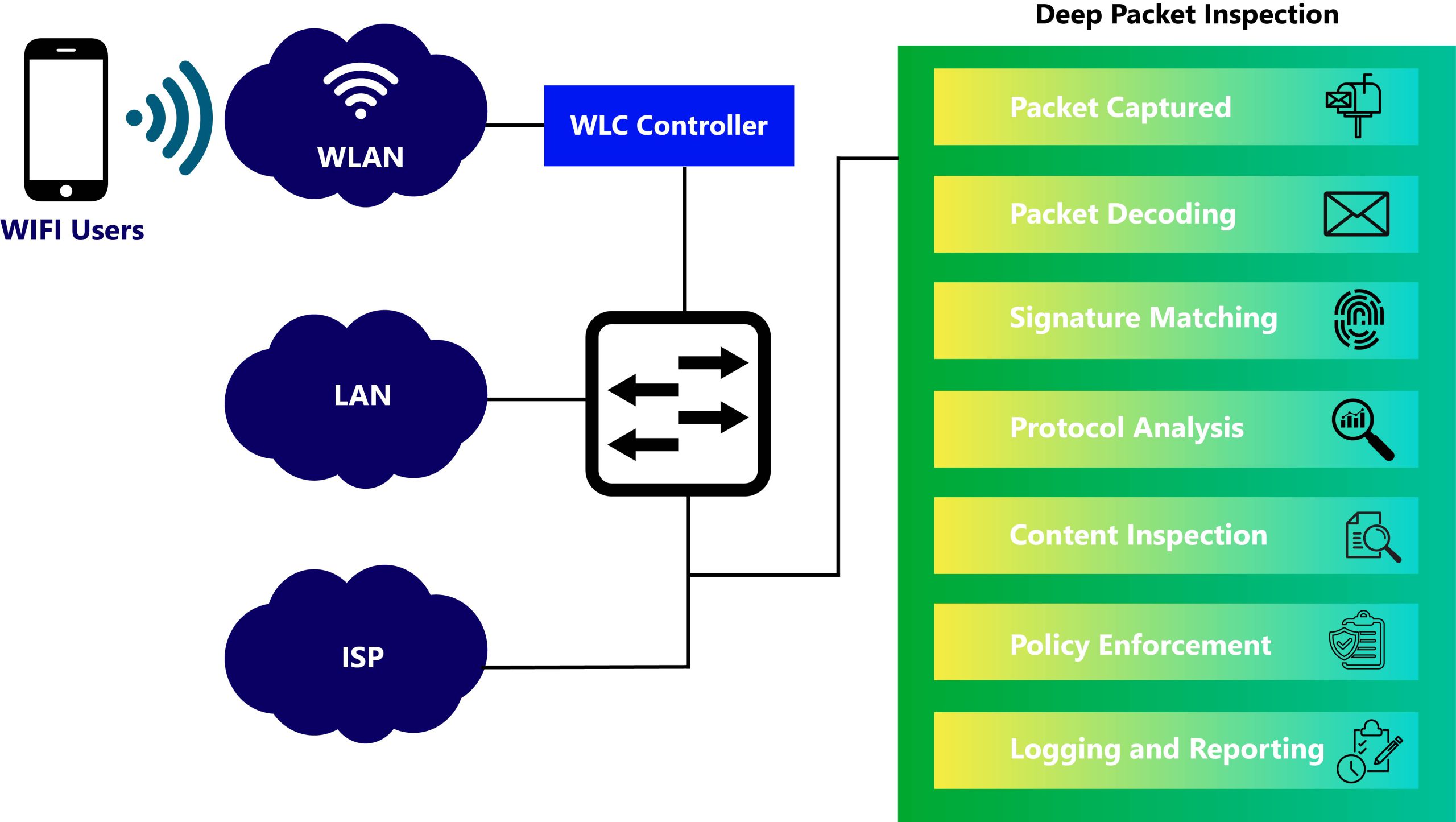
DPI involves the following steps:
- Packet Capture: The DPI system intercepts the packet as it travels through the network infrastructure. This interception can occur at various points in the network, such as routers, switches, or dedicated DPI appliances.
- Packet Decoding: The DPI system decodes the packet to extract its contents, including the header and payload. This process involves parsing the packet according to the relevant network protocols (e.g., TCP/IP, UDP) to understand its structure and format.
- Signature Matching: The extracted packet content is compared against a database of predefined signatures or patterns representing known applications, protocols, or security threats. These signatures can include keywords, regular expressions, or behavioral characteristics.
- Protocol Analysis: If a signature match is found, the DPI system identifies the specific application or protocol associated with the packet. This analysis may involve examining protocol-specific attributes, such as port numbers, packet headers, and payload characteristics.
- Content Inspection: The DPI system may perform deep content inspection for certain types of traffic, especially encrypted or compressed data. This involves decrypting or decompressing the packet payload to analyze its contents more thoroughly. Content inspection allows the DPI system to extract relevant information, such as URLs, email addresses, or file types, for further processing.
- Policy Enforcement: Based on the results of the inspection, the DPI system applies predefined policies or rules to determine how to handle the packet. These policies may include QoS prioritization, traffic shaping, access control, intrusion detection/prevention, or content filtering.
- Logging and Reporting: The DPI system logs information about each inspected packet, including its source and destination, protocol, detected application, and any policy enforcement actions taken. This data can be used for network monitoring, troubleshooting, compliance auditing, and security analysis.
Following these steps, DPI enables network administrators to gain deep insights into network traffic, detect and mitigate security threats, enforce usage policies, and optimize network performance. It provides a powerful tool for enhancing network security, efficiency, and reliability in today’s interconnected world.
Use cases for DPI:
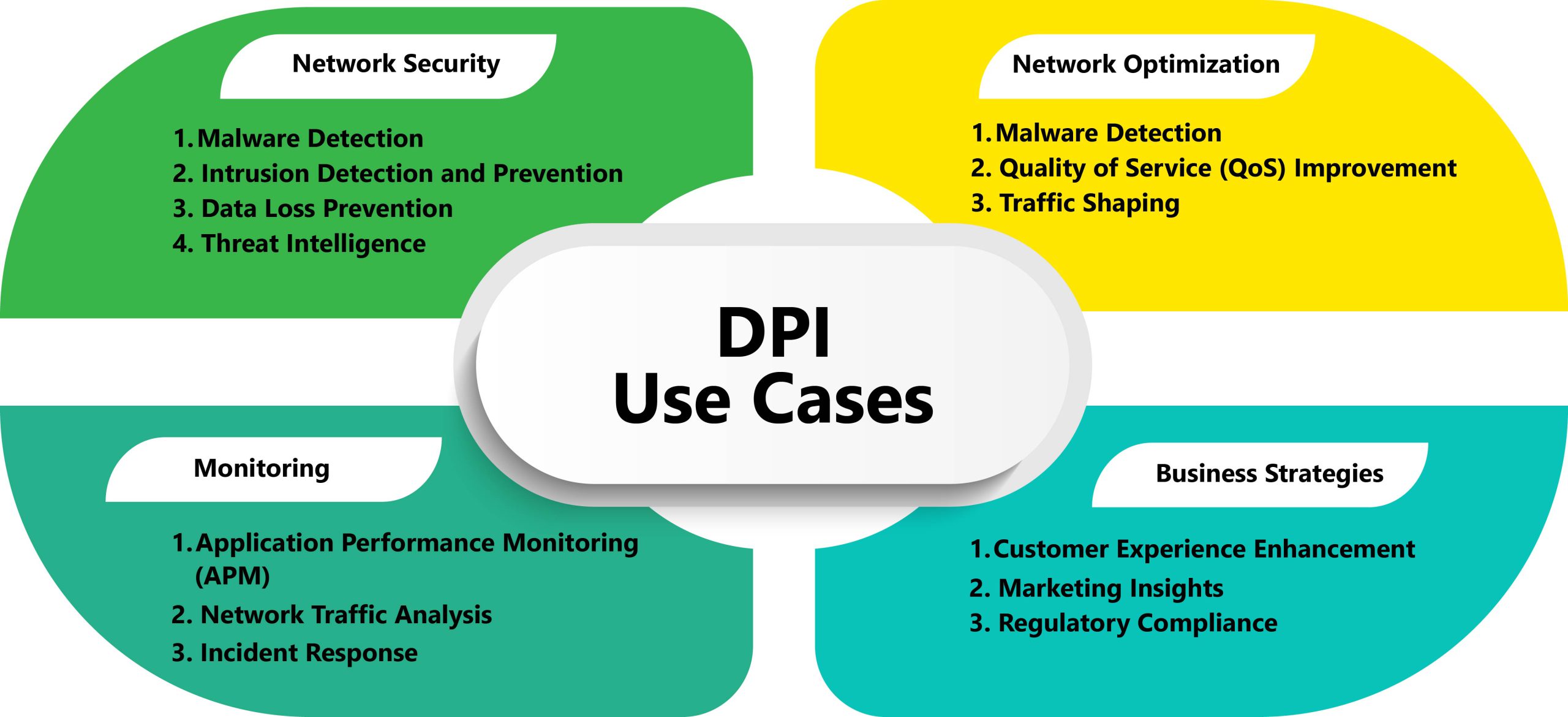
These use cases demonstrate the versatility and effectiveness of Deep Packet Inspection in addressing various network security, optimization, business strategy, and monitoring requirements.
- Network Security:
-
- Malware Detection: DPI can analyze packet content to detect and block malware threats traversing the network.
- Intrusion Detection and Prevention: DPI can identify suspicious activities and potential intrusions, enabling proactive security measures.
- Data Loss Prevention (DLP): DPI helps monitor and control sensitive data transfers to prevent data breaches and ensure compliance with security policies.
- Threat Intelligence: DPI can extract threat intelligence from network traffic to enhance threat detection and response capabilities.
- Network Optimization:
-
- Bandwidth Management: DPI enables network administrators to monitor and control bandwidth usage, prioritize critical applications, and optimize network performance.
- Quality of Service (QoS) Improvement: DPI helps prioritize and manage traffic to ensure high-quality service delivery for critical applications and users.
- Traffic Shaping: DPI can shape traffic flows based on application types, user profiles, or policies to optimize network resources and reduce congestion.
- Business Strategy:
-
- Customer Experience Enhancement: DPI enables businesses to monitor and analyze user behavior, application usage, and network performance to enhance customer experience.
- Marketing Insights: DPI can provide valuable insights into user demographics, preferences, and trends, helping businesses tailor marketing strategies and offerings.
- Regulatory Compliance: DPI assists organizations in complying with industry regulations and data protection laws by monitoring and controlling data flows.
- Monitoring:
-
- Application Performance Monitoring (APM): DPI helps monitor and analyze application performance metrics, such as response time, latency, and throughput, to optimize application delivery and user experience.
- Network Traffic Analysis: DPI enables real-time analysis of network traffic patterns, user behavior, and application usage to identify anomalies, troubleshoot issues, and improve network visibility.
- Incident Response: DPI provides valuable data for incident response teams to investigate security incidents, detect breaches, and mitigate threats effectively.
Benefits of DPI:
- Enhanced Security: DPI’s ability to identify and mitigate threats in real time enhances network security posture.
- Improved Network Performance: DPI contributes to better overall network performance by managing traffic and resources effectively.
- Regulatory Compliance: DPI assists organizations in adhering to industry regulations and data protection standards.
- Resource Allocation: QoS implementation through DPI ensures critical applications receive the necessary resources.
Benefits of DPI in Cloud Environments:
In addition to its traditional use cases, Deep Packet Inspection (DPI) can also play a crucial role in cloud environments. By leveraging cloud-based DPI solutions, organizations can gain visibility and control over network traffic flowing through their cloud infrastructure. DPI in the cloud offers several benefits:
- Scalability: Cloud-based DPI solutions can scale dynamically to accommodate fluctuations in network traffic volume, ensuring consistent performance and analysis capabilities.
- Flexibility: With cloud-based DPI, organizations can deploy and manage inspection policies centrally across distributed cloud environments, promoting consistency and ease of management.
- Cost-Effectiveness: Cloud-based DPI eliminates the need for upfront hardware investments and allows organizations to pay for resources on a usage-based model, resulting in cost savings and operational efficiency.
- Integration with Cloud Security Services: DPI can be integrated with other cloud-native security services, such as cloud access security brokers (CASBs) and cloud firewalls, to provide comprehensive threat detection and mitigation capabilities.
- Compliance: Cloud-based DPI solutions can assist organizations in meeting regulatory compliance requirements by providing visibility into data flows and ensuring adherence to security policies.
Implementing DPI in cloud environments involves deploying DPI sensors or virtual appliances within the cloud infrastructure, configuring them to monitor and analyze network traffic, and integrating with cloud management platforms for centralized control and orchestration. By harnessing the power of DPI in the cloud, organizations can enhance their security posture, optimize network performance, and ensure compliance in an increasingly cloud-centric IT landscape.
Potential Concerns and Considerations:
- Privacy: Deep inspection of packet content raises concerns about user privacy and data confidentiality.
- Net Neutrality: DPI can be used to favor certain types of traffic over others, potentially violating net neutrality principles.
- False Positives/Negatives: The accuracy of DPI largely depends on signature databases, leading to the possibility of false positives or negatives in threat detection.
- Resource Intensive: DPI requires substantial computational resources, which could impact network performance.
- Ethical Use: Using DPI responsibly and transparently is essential to avoid misuse or infringing on users’ rights.
Happiest Minds Expertise in Networking:
Happiest Minds is a leading product & digital engineering services company known for providing Engineering R&D Services to clients. We offer a wide range of Network Testing Services covering the needs of networking OEMs, ISV, and Service providers by leveraging its multi-talented pool, in-house test frameworks, test accelerators, tools, and test servers.
As part of our competency built across many years of project experience, we have expertise in testing & test automation on Deep Packet Inspection (DPI) solutions, covering various DPI use cases, including network security, traffic analysis, and application performance monitoring.
We have provided software services for industry-leading vendors to enhance their DPI platforms to integrate, test, and automate DPI features. Our team has worked on creating comprehensive DPI solutions tailored to meet the specific needs of our clients, including:
– Traffic analysis: Analyzing network traffic at a granular level to identify performance bottlenecks, optimize resource allocation, and ensure Quality of Service (QoS).
– Application performance monitoring: Monitoring and analyzing application performance metrics, such as response time, latency, and throughput, to optimize application delivery and user experience.
We have developed custom test strategies and test automation frameworks to validate DPI functionalities and performance benchmarks. Our in-house test framework, named NTAF, utilizes Python/Robot to automate testing across various network devices and vendors, including open-source options like DANOS.
Conclusion:
Deep Packet Inspection is a powerful tool that network architects utilize to ensure security, performance, and efficient resource allocation within networks. While its benefits are substantial, it’s crucial to balance its use with ethical considerations and users’ rights, thereby creating a network environment that’s both secure and respectful of privacy.

is a Test Architect at Happiest Minds. He has over 13 years of experience in networking, bringing extensive hands-on experience in both manual and automation testing. His expertise lies in networking, ethernet, wireless, and satellite communications.
In his role, Viswesh has taken the lead on various feature releases for an existing customer, focused on the DPI space. He has actively contributed to developing test automation frameworks and has been instrumental in creating, enhancing, and troubleshooting test scripts. Over the course of his 13-year career, Viswesh has collaborated with many global networking companies and successfully delivered network test solutions.




