Today, Penetration testing (aka pen tests) has become an integral part of any cybersecurity system that pre-determines the system’s vulnerabilities and fill those gaps before an external attacker exploits it. Red Teaming is a broader approach to penetration testing that plays a pivotal role using the real-life attacker’s method to test the system if an attack is possible. In contrast, Blue Teaming is typically based on a cybersecurity operation center responsible for defending against organizations cyber-attacks.
Let’s delve into the concept and understand the red and blue team’s approach and challenges and how the purple team’s rise has enhanced the overall vulnerability detection, threat hunting and network monitoring capabilities.
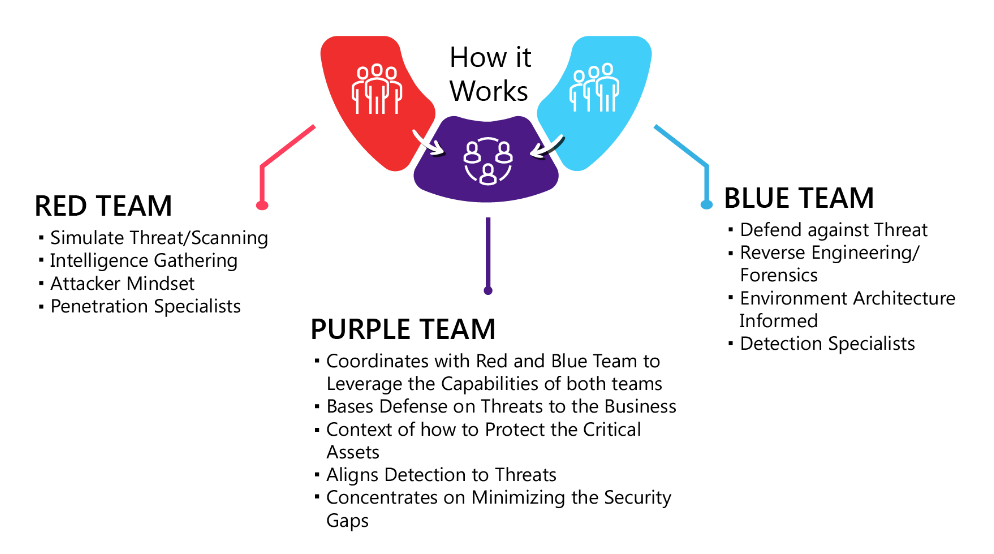
Red Teaming
The Red team performs penetration testing, vulnerability assessment, cyber-attack simulations and more to discover weaknesses in the environment.
Blue Teaming
The Blue Team detects, analyses, and remediates against the threats observed in a cybersecurity operation center console.
The Challenge
Often, this two teamwork separately and in a disconnected manner. There is no communication or discussion medium between the teams to evaluate the results or enhance the security controls aligned with the organization’s threat landscape.
The Need
There are often no continuous response channels between the red and blue teams. Most organizations are adopting short term activities for security gap assessment instead of collaborating and continuously enhancing the security control, failing to leverage red and blue team insight to notify and assess long term security goals and strategy.
The Solution – Purple Teaming
With the introduction of Purple Teaming, the way penetration testing is carried out has changed. It has collaborated the two methodologies of the Red and Blue Team to develop a deception technology in cybersecurity.
What is Purple Teaming? It is a cybersecurity testing exercise in which specialists play both Red Team and Blue Team. The intention is to provide a sturdier, more profound, confident action that delivers a more custom-made, realistic assessment to the organization being tested. The main objective of the exercises by Purple Team is Cyber Threat Intelligence-led, emulating Tactics, Techniques, and Procedures (TTPs) leveraged by known malicious threat actors actively targeting the organization to identify and remediate security gaps in the organization’s security posture.
How it works
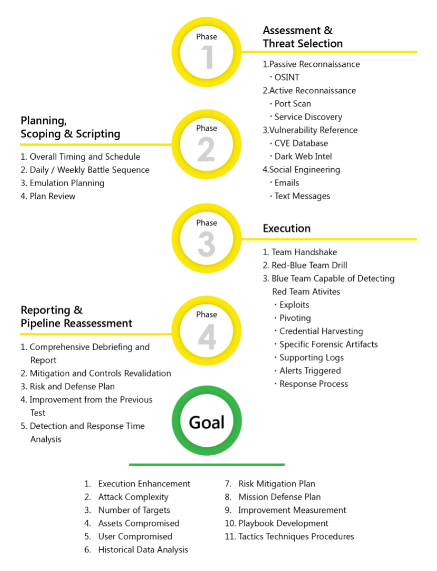
The workflow
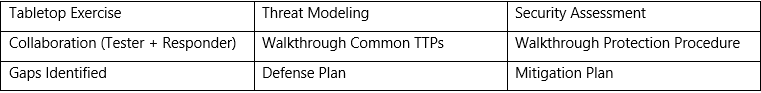
Immediate Steps Towards Enhanced Exercise
Next Three Months
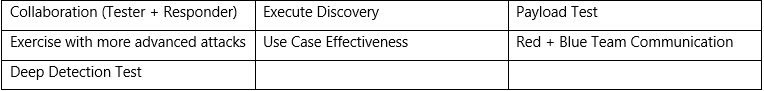
Next Six Months
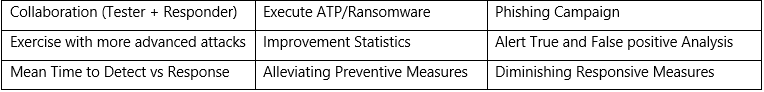
What to be continued
Adversaries have continued to evolve their tactics, techniques, and procedures (TTPs). As they continue to pose security risks with a high impact on business, we must ensure that people, processes, and technology in the environment collaborate for a healthy security posture. Purple Teaming does not need an additional team. It is more about effective collaboration and streamlined and frequent communication between your Red and Blue Teams. As security is everybody’s concern, the continued exercises from Purple Team involve all stakeholders from IT and non-IT and create a more secure environment by minimizing the probable damages due to unintentional mistakes.

has over 15 years of experience in cybersecurity. He is currently handling multiple SOC in Happiest Minds Cyber Risk Protection Platform – A new and enhanced SOC platform to help clients fight against the bad actors. Samit has made a significant contribution in various security design solutioning and mentoring blue teams.







