Over the past few years the risk about data loss has increased exponentially. The key attacking factor for a data loss event is people – they handle electronic data and make mistakes.Data loss could be from any of the aspects such as physical damage or from hack or unauthorized access. Thus, the use of data loss prevention (DLP) solutions has become more and more important to identify critical aspects for protecting organizational data from being leaked to any unauthorized locations. Almost every organization with well-set risk management services as well is facing such a catastrophic scenario currently.
There are multiple forms of data. However, the critical aspect lies in evaluating and identifying the right DLP solution tool irrespective of where the Data resides – in network – on the Cloud or at Endpoints actions.
Some of the standard technological security measures that can be employed for dealing with data leakage incidents are categorized as shown in the fig.
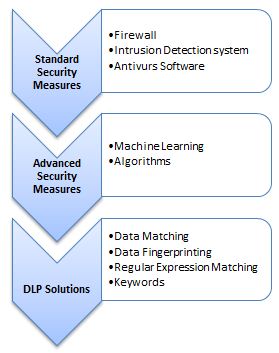
In addition, companies’ should be able to identify and track all these data and maintain a complex operating environment with well-defined DLP strategies to drastically reduce the risk of any data security breaches.
Defining DLP Strategy
The most important strategy would be to identify what type of data needs to be protected and secondly monitoring and detecting the flow of sensitive data throughout the enterprise and finally blocking the sensitive information that doesn’t meet the security policies by using methods like encryption.
Identifying sensitive data
In an organization, Data is stored at different forms in varied locations and it requires identification and the two major techniques used in DLP system to identify such sensitive information is called Data Matching and Data Fingerprinting. The data matching approach basically uses a regular expression to recognize sensitive information that follows a regular pattern. In the fingerprinting approach the system creates an index of the file and compares with the index of all other documents leaving the organization.
The Endpoint and Encryption method
The endpoint DLP approach examines all the information that comes to a user computer and decides what needs to be allowed as per the company policies. It is a very powerful tool for protecting sensitive information. This is also known as an agent-based concept wherein a software agent resides at endpoints of data and detects for any policy violations.
The other most powerful and effective data security method is Encryption, where it translates all the data into codes and makes it password protected. These encrypted data are also known as cipher text. All Data Security components basically use Advanced Encryption Standard (AES) to keep all private data safe.
In summary, organizations should be able to identify the sensitive data and then monitor and protect the sensitive information by integrating it with various endpoints and network based controls. Organizations should also adopt an appropriate DLP strategy and then build a monitoring environment that effectively checks in for data that is violating the companies security policies.

Arnita is a former Happiest Mind and this content was created and published during her tenure.