Managing a BYOD program with due vigilance and risk control is a tricky situation. Though BYOD is a cost effective option for creating a mobile engaged workforce, security concerns surrounding it often lead to enterprises incurring high additional expenses in terms of infrastructure and systems.
BYOD enables huge benefits in terms of convenience and speed. Employees can work at any time, from anywhere with considerable access to information. It also helps companies cut down on technical equipment costs. However, without sufficient security measures in place, confidential information of an enterprise on an employee’s personal gadgets is always a risk. And security methods such as Mobile Device Management (MDM) or Identity and Access Management involve a certain amount of investment. In such a case, how can an enterprise manage a BYOD program, while getting a hold on risks and keep costs at bay?
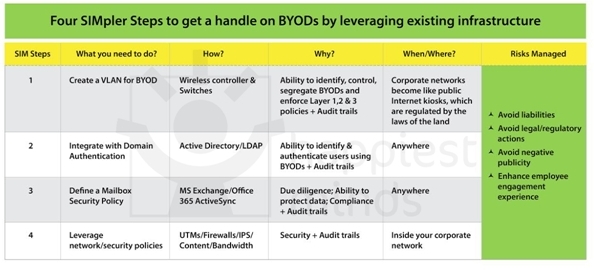
Security systems and tools for an organization are eventually inevitable. But there are some smart tricks that can get you a handle on BYOD using existing infrastructure. And these are mostly at the elementary level.
Here’s what can be done:

Thiruvadinathan is a former Happiest Mind and this content was created and published during his tenure.







